Whether you’re sharing personal documents with family or collaborating on a secret project at work, here’s how to ensure you share files securely.
What is secure file sharing?
Types of file sharing
Why use secure file sharing?
8 tips for secure file sharing
1. Use end-to-end encryption
2. Choose a privacy-focused provider
3. Use strong passwords
4. Turn on two-factor authentication (2FA)
5. Password-protect files
6. Set sharing time limits
7. Monitor file access
8. Use a VPN on public WiFi
Share files securely for free
What is secure file sharing?
Secure file sharing means sharing files securely and privately so they’re only accessible to the intended recipient(s).
From intimate personal notes to medical records, banking details, and legal documents, your files contain sensitive information(new window) you must keep private and secure. But some files you need to share and share securely.
Types of file sharing
Here are the most common ways to share files, though not all are secure or practical.
Removable storage
The old-fashioned way of ensuring your files reach only the intended recipient is to copy them onto a USB drive and hand it to them. But you must ensure the removable drive is encrypted with a strong password in case it gets lost.
While this remains a secure way of transferring files, it’s hardly practical in most cases. And once you’ve handed over the drive, you can’t update the file or control access to it.
File Transfer Protocol
Originally developed to transfer files from one computer to another, File Transfer Protocol (FTP)(new window) is still used today to share files on computer networks. As it wasn’t designed to be secure, people usually use encrypted FTPS(new window) or SFTP(new window) instead.
However, as FTP servers and clients are complicated to set up and use, it’s not a practical file-sharing solution for most people.
Peer-to-Peer (P2P)
P2P file sharing(new window) uses a decentralized network of “peers” that can be used to share information. With P2P, you can share documents, audio files, video files, or even software and video games.
P2P file sharing was designed to distribute resources on the internet and help connected devices work together. So while it’s good for distributing files like software and music, it’s not designed for sharing sensitive files. And it will expose your IP address to the recipients of your files unless you use a virtual private network (VPN)(new window).
Email attachments
The easiest way to share a file with someone is to attach it to an email. Remember, though, that most big email providers, like Gmail and Outlook, aren’t wholly secure.
They use TLS encryption(new window) to secure an email in transit. But, as Microsoft explains(new window), “the message might not stay encrypted after the message reaches the recipient’s email provider”. And the providers hold the encryption keys to your messages, so you never know who might access them.
But you can send sensitive files by email using end-to-end encrypted email, like Proton Mail.
Cloud-based secure file sharing
If you want to securely share larger files or whole folders, secure cloud storage is a good solution.
Instead of sending the files, you can send a secure link to them or a folder containing the files stored in the cloud. The recipient then clicks on a button to download the files, like this example from Proton Drive.
With the best secure cloud storage, you can share files of any size, protect them with passwords, set sharing time limits, and more.
Why use secure file sharing?
Whether at work or home, you’ll need to share sensitive files securely sometime. And if you run a business, finding a secure file-sharing solution is essential, and not just for security.
Here’s why cloud-based secure file sharing can be useful for anyone — for work or play.
Keep your data secure
The most secure cloud storage is end-to-end encrypted. That means no one but you and those you share files with can access them.
Transfer large files
Sending files by email isn’t secure. Even if you use encrypted email, attachment sizes are usually limited to around 25 MB. With the best secure file storage, you can share files of any size.
Stay in sync
Sharing files with secure cloud storage allows you to update files on the fly, as everyone shares the same encrypted copy. Whether collaborating at work or sharing a folder with family, you’ll all have the latest version.
Monitor access
When you send a secure file-sharing link, you have a record of when you share a file or folder. And with some providers, you can track whether it’s been downloaded, set sharing time limits, and revoke access to it.
Be compliant
If you run a business, you’ll have confidential business information you need to protect. Secure cloud storage ensures you comply with data privacy laws like HIPAA and GDPR(new window).
8 tips for secure file sharing
Most big cloud storage providers, like Dropbox or Google Drive, encrypt files in transit or at rest on their servers. But your files aren’t end-to-end encrypted, and the provider holds the encryption keys.
That means providers can decrypt and access your files, so you can’t be sure who might access them. And if your provider suffers a data breach(new window), a hacker could steal the keys to your files. So most cloud storage isn’t secure enough to share your sensitive files.
Here’s what to look for when choosing and using a secure file-sharing service based in the cloud:
1. Use end-to-end encryption
Make sure your files are end-to-end encrypted. With end-to-end encryption, you hold the encryption keys to your files, so only you and the people you share them with can access them.
2. Choose a privacy-focused provider
Choose a provider based in a country with strong data privacy laws, so your files are protected. And before signing up, read the privacy policy to see how they handle your data. If your files are end-to-end encrypted, the provider won’t be able to access them or share them with third parties.
3. Use strong passwords
As with any online account, use strong passwords or passphrases to secure your files. Use a good open-source password manager to help you generate and store passwords securely.
4. Turn on two-factor authentication (2FA)
Switch on two-factor authentication (2FA) to give your files an extra layer of security. With 2FA, you must verify your identity by entering a six-digit code from an authenticator app or activating a physical security key. Using a strong password with 2FA is essential to secure any online account.
5. Password-protect files
Protect secure file-sharing links with a password so only people with the password can download your files. Choose a strong password and send it via a secure messaging channel, or just tell the recipient in person.
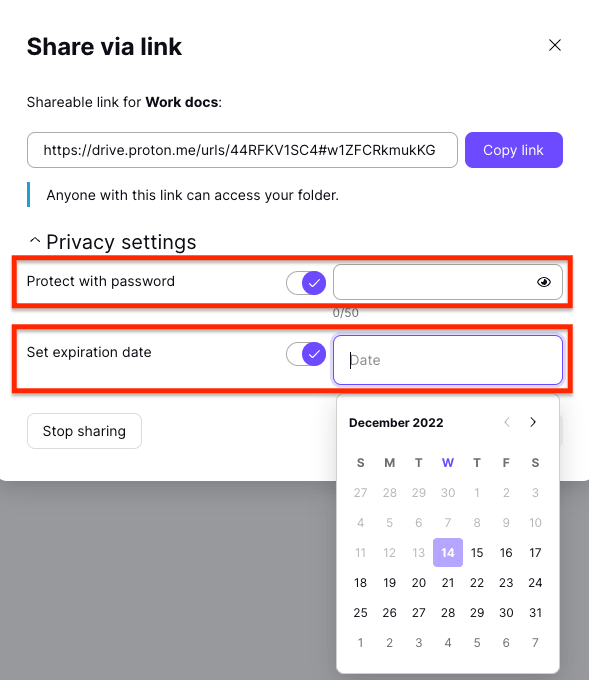
6. Set sharing time limits
Some file-sharing providers allow you to set an expiration time after which the link will no longer work. Set only the time you need to share the files to minimize risk. For example, it’s easy to add a password and expiration date with Proton Drive:
7. Monitor file access
Monitor your shared files and folders for suspicious activity and control access. With Proton Drive, you can track the number of times they’ve been downloaded and revoke access with one click.
8. Use a VPN on public WiFi
WiFi hotspots in coffee shops, libraries, and other public places are often insecure. So it’s worth using a trustworthy VPN(new window) to encrypt your internet traffic whenever you’re on public WiFi, especially when handling confidential information.
Share files securely for free
One of the easiest and most secure ways to share files is to use Proton Drive: Securely share files of any size with anyone for free.
Upload your files to Proton Drive, and they’re encrypted automatically with end-to-end and zero-access encryption. That means no one but you can read them, not even Proton. And we’re based in Switzerland, so they’re protected by some of the strongest privacy laws in the world.
With Proton Drive, you can:
- Share files securely: Create secure links to share files or folders of any size with anyone, even if they’re not on Proton Drive.
- Password-protect files: Lock down your sharing links with a strong password.
- Set sharing time limits: Set an expiration date for file sharing to minimize risk.
- Monitor and revoke access: Track the number of downloads and stop sharing with one click.
- Protect your account with 2FA: Verify your identity with an authenticator app or security key.
- Securely access and share anywhere: Get Proton Drive mobile apps for all your devices.
Proton Drive includes free access to Proton Mail, Proton Calendar, and Proton VPN(new window), and you can get started for free.
If you want more storage or would like to support our goal to give everyone privacy and security online, get a paid account. Together, we can build a better internet where privacy is the default.








